| Training | Mode | Training -quality Ratings |
| Software Composition Analysis (SCA) – OWASP Dependency Check / Jfrog Xray | Instructor-led online | 5/5 |
| Runtime application self-protection & Containers (RASP) – Falco / Notary / The Update Framework (TUF) / Nikto | Instructor-led online | 5/5 |
| Web Application Firewall (WAF) – AWS WAF / Azure Web Application Firewall / Cloudflare Web Application Firewall (WAF) | Instructor-led online | 5/5 |
| Securing Credentials – HashiCorp Vault & AWS Secrets Manager, Azure key vault, AWS KMS, Kubernetes Secrets | Instructor-led online | 5/5 |
| Policy-based control for cloud native environments – Open Policy Agent (OPA) | Instructor-led online | 5/5 |
| Cloud Security service & Practices – Cloud Security with AWS & Azure service | Instructor-led online | 5/5 |
| Security Information and Event Management SIEM – Splunk SIEM | Instructor-led online | 5/5 |
| Webserver – Apache HTTP & Nginx | Instructor-led online | 5/5 |
| Multi-cluster Kubernetes orchestration platform – Rancher | Instructor-led online | 5/5 |
| Services mesh Data planes & Control Planes – Envoy & Istio | Instructor-led online | 5/5 |
Software Composition Analysis (SCA) – OWASP Dependency-Check / Jfrog Xray

OWASP dependency-check is a free and open-source OWASP solution. At the moment, a dependency check can be used to examine applications for the use of known vulnerable components.
JFrog Xray is a software quality assurance (SQA) platform that incorporates security into your DevOps operations, allowing you to produce trusted software releases more quickly.
This training will help you to learn all the required skills and knowledge about Dependency Check and Jfrog Xray. This is an instructor-led online training, structured to enable you to learn from our best IT trainers who are well-trained and certified experts and hold 16+ years of experience in IT. This training is applicable all over the world. Whoever wants to learn about Jfrog Dependency-Checky Check doesn’t matter if you are a beginner or an experienced professional. Get trained with us and start your career.
Runtime application self-protection & Containers (RASP) – Falco / Notary / The Update Framework (TUF) / Nikto
Falco is an open-source solution for detecting ongoing risks and threats in Kubernetes, containers, and the cloud. Falco is a security camera that detects strange behavior, configuration changes, intrusions, and data theft in real-time.
The Update Framework (TUF) assists developers in maintaining the security of software update systems, including protection against attackers who obtain access to the repository or signing keys.
Nikto is a Perl-based open-source program that scans a web server for vulnerabilities that can be exploited and used to attack the site. It can also detect problems with specific version details of over 200 servers and check for outdated version details of 1200 servers.
This training enables you to learn about all these four courses’ concepts, features, and functionalities. Our training offers you instructor-led online training to get trained by our best IT trainers. They hold more than 16 years of IT experience. This training course curriculum has been made as per IT standards. If you are looking for the best institute, then you are at the right place. 60 Hrs Self-paced Videos, Projects, certification, flexible schedule, technical support, learning materials, and many more you get in this training.
Web Application Firewall (WAF) – AWS WAF / Azure Web Application Firewall / Cloudflare Web Application Firewall (WAF)
AWS WAF is a web application firewall that helps protect your online applications or APIs from common web exploits and bots that might disrupt service, compromise security, or waste excessive bandwidth.
Azure Web Application Firewall is a cloud-native service that protects your web applications from bot attacks and common web vulnerabilities such as SQL injection and cross-site scripting.
The Cloudflare web application firewall (WAF) is the cornerstone of our sophisticated application security offering, which keeps apps and APIs secure and productive while thwarting DDoS attacks, detecting abnormalities and malicious payloads, and monitoring for browser supply chain attacks.
This training is structured to let you aware of security stuff so you can protect your systems. We will help you to learn everything about AWS, Cloud flare, and Azure security, through our instructor-led online training, led by our best expert trainers, who have 15+ years of experience in IT. Our training is designed in such a way that you can interact with your instructor to get better training and learning experience. Additionally, we will help you more with 1 project, 60 Hrs Self-paced Videos, 1 Project, certification, a flexible schedule, technical support, learning materials, and many more.
Securing Credentials – HashiCorp Vault & AWS Secrets Manager, Azure key vault, AWS KMS, Kubernetes Secrets
HashiCorp Vault is a secret management tool specifically designed to control access to sensitive credentials in a low-trust environment. It is also used to store sensitive values and at the same time dynamically generate access for specific services/applications on lease.
AWS Secrets Manager helps you protect secrets needed to access your applications, services, and IT resources.
Azure Key Vault is a cloud service for securely storing and accessing secrets.
AWS KMS is a safe and dependable service that protects your keys with hardware security modules that have been validated under FIPS 140-2 or are in the process of being validated.
Secrets are Kubernetes objects that are used to store sensitive data encrypted, such as user names and passwords.
In this training, you will get to know about these concepts, utilization, and processes to get all the information and skills, so you can make yourself an experienced professional, so has ready to use knowledge and skills to perform all the required tasks important to perform for your organization. This is instructor-led online training, led by one of the best IT trainers to train you as a certified professional. your learning experience will be top-notch as we will help you learn in many ways, like class recording, live sessions, PDFs, slides, technical support, and many more. Providing quality training is our main goal.
Policy-based control for cloud-native environments – Open Policy Agent (OPA)
The Open Policy Agent is a general-purpose policy engine that unifies policy enforcement across the stack. Open Policy Agent provides a high-level declarative language that lets you specify policy as code and simple APIs to offload policy decision-making from your software.
This training is designed to teach you about its concept, and how it works through our instructor-led online training, led by our best IT trainers who will help you gain all the required knowledge and skills. The key factor of this training is the quality. To maintain the quality we provide you with the best trainers and every possible way to help you learn the inefficient way. That’s why here you can interact with your trainer to have the best experience. Class recording, live sessions, PDFs, slides, technical support, Interview-kit, and many more, you get in this training as an add-on benefit. Join us to leverage this opportunity.
Cloud Security service & Practices – Cloud Security with AWS & Azure service
In this AWS security, you will be benefited from AWS data centers and a network architected to protect your information, identities, applications, and devices. With AWS, you can improve your ability to meet core security and compliance requirements, such as data locality, protection, and confidentiality with its comprehensive services and features.
With Azure, you can Protect data, apps, and infrastructure quickly with built-in security services in Azure that include unparalleled security intelligence to help identify rapidly evolving threats early – so you can respond quickly.
In this training, you will be taught about the security services and practices of AWS and Azure, and how to leverage them to protect your data and identities. This is an instructor-led online training structured to provide you best training experience by letting you interact with your instructor and provide you with all the required skills and knowledge. We will help you become a professional in this domain. Additionally, you will get 1 project, Class recording, live sessions, PDFs, slides, technical support, Interview-kit, and many more, in this training.
Security Information and Event Management SIEM – Splunk SIEM
Splunk is an analytics-driven SIEM tool that collects, analyzes, and correlates high volumes of network and other machine data in real-time. Splunk gives security teams the relevant and actionable data they need to respond to threats faster and maintain a secure security posture at scale.
This training will help you to understand the security infrastructure of Splunk as well as how its intelligence helps in responding to the threats. This training is designed to help you with all required skills and knowledge, so you can leverage these skills to get a better job in Top MNC companies. This is an instructor-led online training led by our best IT trainers who hold 16+ years of experience in IT. You can leverage their skills and knowledge to gain complete knowledge in this Splunk SIEM. You will also be given 1 project, Class recording, live sessions, PDFs, slides, and many more, after being part of this training.
Webserver – Apache HTTP & Nginx
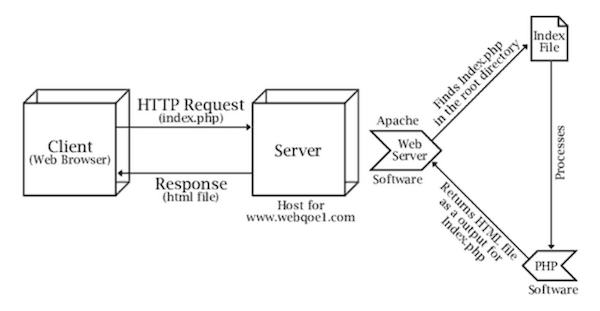
The Apache HTTP Server is an open-source web server that uses the internet to deliver web content.
NGINX is open-source software for web serving, reverse proxying, caching, load balancing, media streaming, and more. It began as a web server that was optimised for speed and stability.
This training will help you understand these two webserver concepts and functions. This is an instructor-led online training where you can interact with your trainer, to have a better training experience. You can ask any question and clear your doubts during this training. This training comes with the best IT trainers to give you all the required skills and knowledge. Our trainer has 16+ years of IT experience. Giving you high-quality training is our motto, that’s why we have brought all possible ways to teach and help you, like 1 project, Class recording, live sessions, PDFs, slides, and many more.
multi-cluster Kubernetes orchestration platform – Rancher
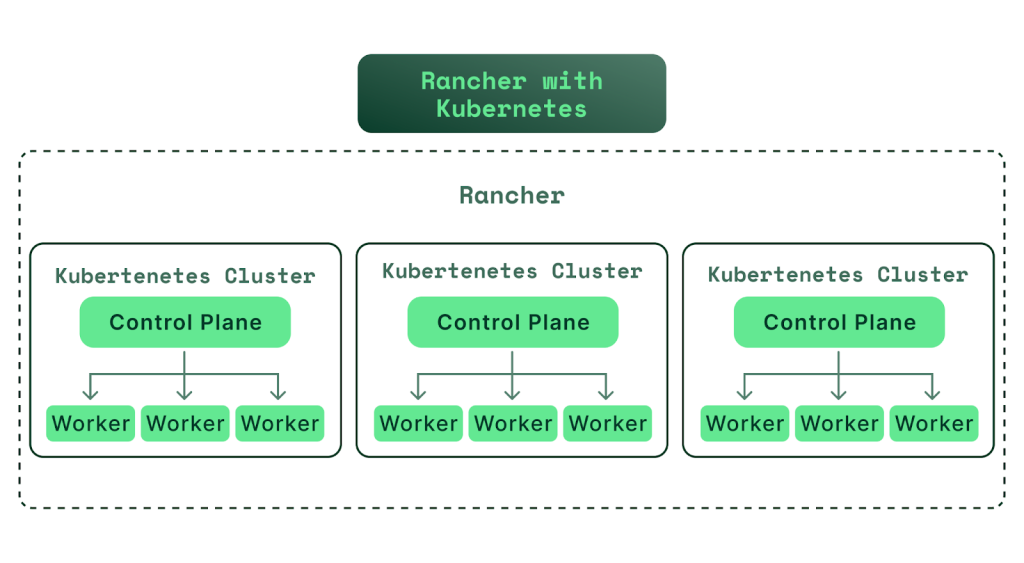
Rancher is a container-adopting team’s whole software stack. It helps DevOps teams manage numerous Kubernetes clusters while also providing integrated tools for executing containerized workloads.
In this training, you will gain complete knowledge about Rancher concepts and it helps in finding challenges or let you run Kubernetes everywhere. This is an instructor-led online training, led by our expert trainers to give you all the required knowledge and skills, also have 16+ years of IT experience. Providing you with an expert trainer is a part of our strategy to maintain the quality of this training. Get enrolled and become a part of the professional world who knows Rancher. Also, get 1 project, Class recording, live sessions, PDFs, slides, and many more in this training.
Services mesh Data planes & Control Planes – Envoy & Istio
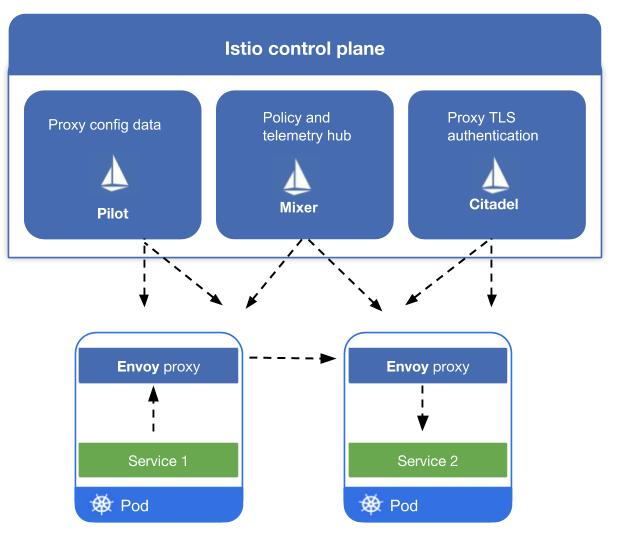
Envoy is a high-performance C++ distributed proxy designed for single services and applications, as well as a communication bus and “universal data plane” designed for large microservice “service mesh” architectures.
Istio enables enterprises to protect, connect, and monitor microservices, allowing them to more quickly and safely upgrade their corporate apps.
This training will let you learn about both Istio and Envoy together, and how both work with each other. This training is designed to help you gain all the required skills and knowledge like data planes get deployed as sidecars. This is instructor-led online training, structured to give you an immersive training experience, by letting you interact with your trainer, so you can feel the same as you will feel in the classroom. having this training you will become a professional in this work. Also, we will help you in many ways by providing you with real-time-based projects, Different learning materials, class recordings, technical support, and many more.