Source – techtarget.com A new password guessing technique takes advantage of machine learning technologies. Expert Michael Cobb discusses how much of a threat this is to enterprise security. What happens when authentication and access control measures are attacked by adversaries equipped with machine learning? This question has been examined in a couple of recent university studies, and Read More
Year: 2017

Source – universityaffairs.ca Governments can have a pretty dismal track record when it comes to predicting the next big thing. Tax dollars spent on visionary projects are often, it seems, tax dollars thrown away. But, this past spring, Ottawa might have made its best bet yet with the $125 million it has set aside over the Read More
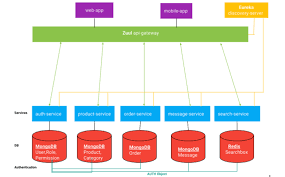
Source – techrepublic.com Ask what Amazon’s greatest accomplishment has been to date, and you’ll probably hear about how they’ve revolutionized online shopping, or become a credible player in media and entertainment. If you speak with a technologist, they might mention Amazon’s emergence as one of the preeminent technology platforms. While there’s nothing new or exciting about Read More

Source – forbes.com Algorithms are incredible aids for making data-driven, efficient decisions. And as more industries uncover their predictive power, companies are increasingly turning to algorithms to make objective and comprehensive choices. However, while we often rely on technology to avoidinherent human biases, there is a dark side to algorithm-based decisions: the potential for homogenous data sets to produce Read More

Source – techcentral.co.za Not much time passes these days between so-called major advancements in artificial intelligence. Yet researchers are not much closer than they were decades ago to the big goal: actually replicating human intelligence. That’s the most surprising revelation by a team of eminent scholars who just released the first in what is meant to be Read More

Source – jaxenter.com Data Science, Machine Learning, and Artificial Intelligence are attracting big money today. Many organizations, big and small, are investing millions in research — and people — to build powerful data-driven applications. Python and R have long been the two languages said to have a hold on the data science world, but that’s not Read More

Source – cio.com.au There’s a significant level of hype around machine learning – generated by tech vendors, the media, and even CIOs themselves. But putting the hoopla aside, machine learning technologies actually have real substance and as a CIO, it’s worthwhile getting on top of the trends in this area. So what’s all the fuss about? Read More
Source – iflscience.com Epilepsy can be a debilitating condition, even for those who experience seizures infrequently. Sufferers may be afraid to drive or even go out in public, even though their episodes may be as rare as less than once a month. So a device that gives warning of when attacks are likely could be transformative. Work Read More
Source – nydailynews.com The internet changed travel planning for most people years ago, but even a high-powered search engine has its limitations when it comes to plotting out the perfect weekend getaway or lengthy European excursion. Yes, an online search provides plenty of travel options. In fact, it may be too many, so that the would-be Read More
Source – yourstory.com Data Science may have become hot in this decade, but its existence can be traced back to more than a couple of decades ago. A lot of academic research took place in data science (data mining) then, but there was no application in the market; it was all theoretical and mathematical. Real change came Read More

Source – phys.org In artificial intelligence (AI), machines carry out specific actions, observe the outcome, adapt their behavior accordingly, observe the new outcome, adapt their behavior once again, and so on, learning from this iterative process. But could this process spin out of control? Possibly. “AI will always seek to avoid human intervention and create a Read More

Source – ndtv.com SAN FRANCISCO: Facebook Inc will expand its pattern recognition software to other countries after successful tests in the U.S. to detect users with suicidal intent, the world’s largest social media network said on Monday. Facebook began testing the software in the United States in March, when the company started scanning the text of Read More

Source – forbes.com In part one of this two-part series, we covered the complexity of the digital identity problem and some early-market solutions. Read on for part two below! Machine Learning In Digital Identity Two broad categories of machine learning models are clustering (unsupervised learning) and classification (supervised learning). Each of these has its pros and cons and, Read More

Source – techtarget.com For the average worker, particularly the mobile worker, both the complexity of tools and the need for consultation with experts make it difficult to realize productivity improvement through analytics. However, microservices may hold the key to solving this problem. Since applications are being driven to microservice form by increased needs for context-sensitive work Read More

Source – cio.com.au In IT, the bigger the hype, the greater the misconceptions, and data analytics is no exception. Analytics, one of the hottest facets of information technology today, can result in significant business gains, but misperceptions can get in the way of a smooth and timely delivery of analytical capabilities that might benefit business users Read More
Source – ndtv.com Helsinki: Cyber security companies are turning to artificial intelligence and machine learning tools to ward off growing number of attacks on networks, Finland-based internet security firm F-Secure said. As the world is fast moving towards Internet of Things and connected devices, deployment of artificial intelligence (AI) has become inevitable for cyber security firms Read More

Source – dailypioneer.com Cyber security companies are turning to artificial intelligence and machine learning tools to ward off growing number of attacks on networks, Finland- based internet security firm F-Secure said. As the world is fast moving towards Internet of Things and connected devices, deployment of artificial intelligence (AI) has become inevitable for cyber security firms Read More

Source – androidauthority.com After helping to define the modern internet era with Search and Android, Google is already at the forefront of the next wave in computing research and development: AI. Many consider artificial intelligence and neural network computers to be the next step in computing, enabling new use cases and faster computation to solve currently Read More

Source – theguardian.com Once upon a time, a very long time ago – 2009 in fact – there was a brief but interesting controversy about the carbon footprint of a Google search. It was kicked off by a newspaper story reporting a “calculation” of mysterious origin that suggested a single Google search generated 7 grams of CO2, which is about Read More

Source – ibc.org AI is a technology on the cusp. While nothing actually new in itself, a recent convergence of increased computational power with a mushrooming of large datasets and the refinement of existing understanding of the techniques involved has seen it become an important differentiator in the industry. Following a breakthrough year in 2015 when Read More
Source – mediaupdate.co.za Machine learning allows the algorithms that software and systems use to evolve as they process new data. Contrary to what many people think, humans play an integral role in this process and in applying machine learning-driven solutions to real-world problems. Machine learning allows systems and AI engines to automatically learn and improve from experience. Read More
Source – itproportal.com In the world of microservices, the goal is to have a small piece of software that performs a well-defined set of tasks. Microservices are software applications that are self-contained. They are small, independently deployable modular services that run a unique process and communicate through a well-defined, lightweight mechanism to serve a specific goal. Read More

Source – techspective.net For most businesses today, data management has shifted from an important competency to a critical differentiator and determines industry winners and has-beens. Government bodies and Fortune 1000 companies benefit from the innovations of web developers. These organizations are reevaluating existing strategies and defining new initiatives to transform their businesses using “big data”. These Read More

Source – thenational.ae In his 1990 book The Age of Intelligent Machines, the American computer scientist and futurist Ray Kurzweil made an astonishing prediction. Working at the Massachusetts Institute of Technology (MIT) throughout the 1970s and 1980s and having seen firsthand the remarkable advances in artificial intelligence pioneered there by Marvin Minsky and others, he forecast that a computer Read More

Source – irishtimes.com If ever there was an industry ripe for disruption it is surely the legal profession. Unlike many other sectors, however, it has tended to be a little reticent about embracing technology to innovate. This isn’t too surprising. After all, the traditional way of doing business for legal firms has been extremely profitable. The Read More

Source – manitobacooperator.ca An expedition through published and unpublished studies on neonicotinoid pesticides has led a Guelph research team to find no colony-level risk to honeybees from the seed treatments — if they’re correctly used. The University of Guelph team, led by toxicologist Keith Solomon and adjunct professor Gladys Stephenson, analyzed 64 papers from “open, peer-reviewed Read More

Source – opensource.com I struggled with writing the title for this post, and I worry that it comes across as clickbait. If you’ve come to read this because it looked like clickbait, then sorry.1 I hope you’ll stay anyway: there are lots of fascinating2 points and many3 footnotes. What I didn’t mean to suggest is that microservices cause security problems—though like any component, Read More

Source – cio.economictimes.indiatimes.com Insurance has become an extremely competitive market! While there are several players, customers are increasingly becoming aware about what they need. They are now seeking a more individualized experience and if you cannot provide it, rest assured they will find another company that does. So, how do companies find ways to address the Read More

Source – moneycontrol.com Does “Numerophobia” sound familiar? In case you have missed out on this word before, let me enlighten you. This represents the fear of numbers. If you were anything like me with sheer hatred towards mathematics or one of those back-benchers that dreaded the math lecture, appearing for the final exam must have been Read More

Source – securityboulevard.com The terms “artificial intelligence” and “machine learning” are often used interchangeably, but there’s a huge technical difference between them. While the first is used by Hollywood when depicting self-aware machines, the latter is comprised of finely tuned single-task algorithms that are nowhere near self-aware. In cyber security, machine learning algorithms can learn by Read More
